All of our enterprise-grade servers come
equipped with flash drives, ensuring
lightning-fast performance and speed
for your servers and applications.


Cloud Hosting, Vmware Hosting, Managing And Consulting Services.

Cloud
VM
Cloud Object Storage
Flash Object Storage
Cloud Load Balancer
Cloud WAF
Cloud Mail Security Getway
Cloud Backup Application
Cloud Data
CloudEdge and SAP: A Winning Combination for Your Business.
Let us take your business to the next level with CloudEdge
and SAP working together. Host your SAP applications on
our secure servers for improved performance and peace of mind.
We also offer SAP application, platform, and database
deployment services, boosting cost-effectiveness, security,
and efficiency. Read More

Our powerful ingredients make it possible.
3D memory ECC memory
& opt-in memory.
Intel ® Xeon ® Scalable
processors.
WP provides only
flash disk.
VPN.
Fully reserved
memory.
Dell EMC & NetApp
storage.
Dedicated
Bandwidth.
Load balancers.
Latest hardware.
VMware hypervisor.
Network provides
the fasten network
on earth up to 100 GB.
All of our enterprise-grade servers come
equipped with flash drives, ensuring
lightning-fast performance and speed
for your servers and applications.
With data centers located in multiple
locations worldwide, we guarantee
100% uptime, meaning that all of
your servers and applications are
always up and running.
Our capable and experienced team of
engineers is available around the
clock, 24/7/356, to provide technical
assistance and resolve any issues that
may arise via phone, email, or remote
session support as needed.
Our data centers are strategically located in well-connected countries with
state-of-the-art setups, ensuring minimum network latency and the
highest level of performance.
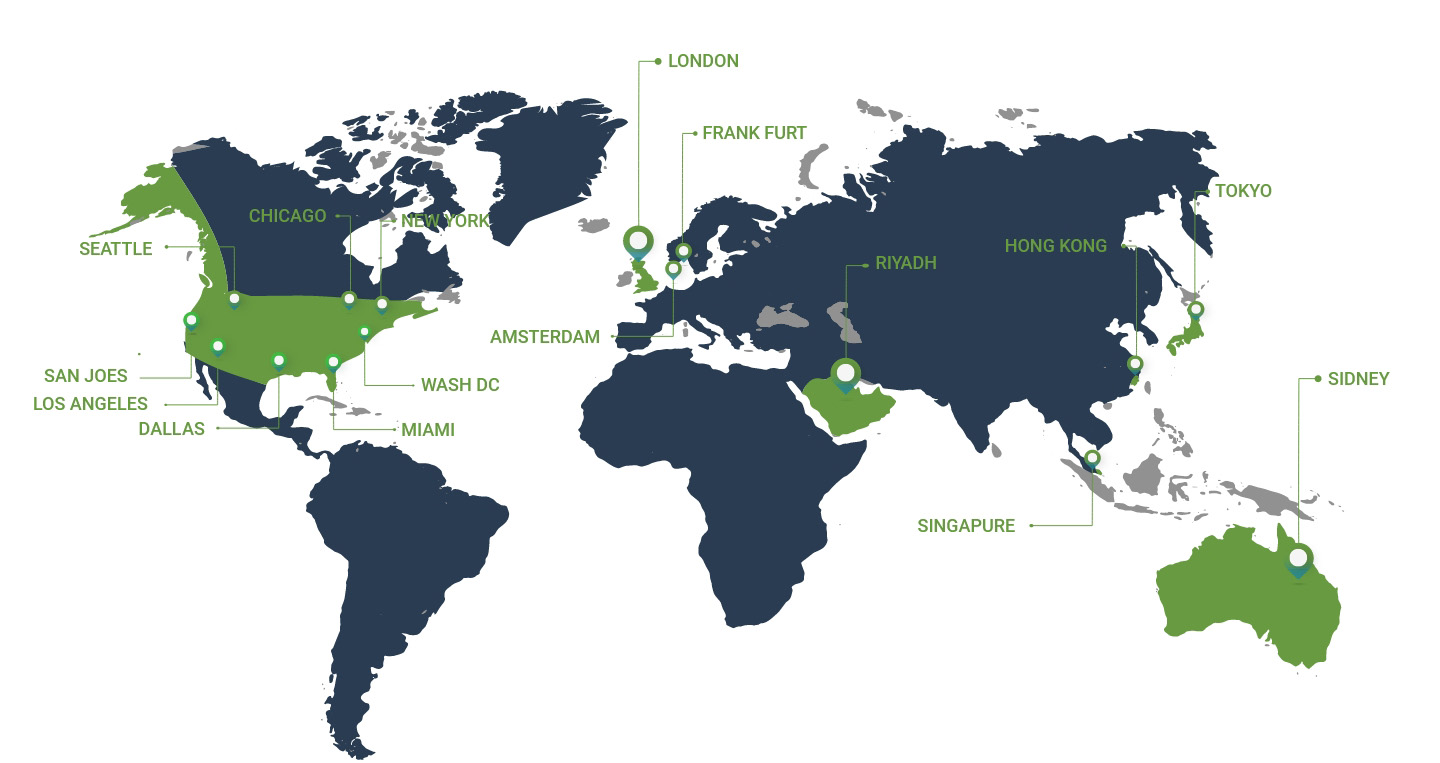
Availability zones are located at 35 points around the world.
Preset By CloudEdge.
For Specific App Files/Settings.
![]()
Set By The Admins.
The Fail-Option To Keep You Going.
Unparalleled Advanced Features.
With our team of certified security experts, we offer round-the-clock, year-round protection for your systems and networks, safeguarding them against any potential threats.
What do We do?
Our Services Include But Are Not Limited To:

Our Filtering And Inspection Systems Filters Out Fake Url Requests (By Application, Source, Destination IP, IP Protocol, Or By Destination Port For TCP And UDP Traffic) Only Allowing Legitimate Addresses To Pass Across The Security Perimeter.
Our Firewall Systems Track And Store Historical Network Activity To Continually Monitor And Report On The Network’s Speed, Health, And Status.
Our Firewall Systems Allow You To Prevent Access To Your Network By Blocking IP Addresses Coming From Specific Geolocations, Even in Entire Countries.
To Increase The Power Of Your Systems, We Offer A Load Balancing Feature For Distributing Data Load Between Multiple Servers.
Right click to build & launch
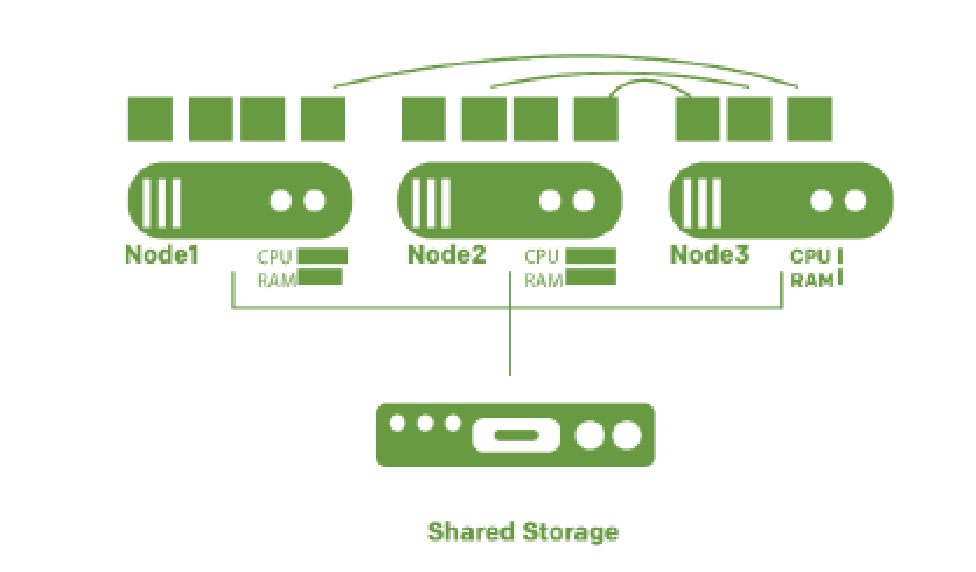
CloudEdge control panel gives you full control features
Host any enterprise-level applications

Host Any Enterprise-Level Applications






At WorldPosta, we provide you with cutting-edge cloud performance monitoring tools that proactively identify any performance bottlenecks in your cloud infrastructure and technologies. Our comprehensive suite of monitoring tools ensures successful service delivery, allowing you to meet your business goals with confidence.

Need To Know The Best Fit To Your Business?

Thank you for your message. It has been sent.
DoneOooops
Something went wrong, please try again
